Reverse engineering a BLE CO₂ sensor
<Back2024-07-10
My employer recently gave away old COVID era CO₂ sensors that were used during the pandemic to infer the exposure level of certain room by measuring CO₂.
CO₂ sensors are typically expensive, so I figured I'd grab a couple. Here's how they look like.

As a standalone device they're fine though their batteries are terrible. It doesn't look like they're very precise as the two devices I was given show measures that are surprisingly different: I've measured a delta of 100ppm of CO₂, and a couple degrees.
Now having said that, wouldn't it be cool if I could connect these to my HomeAssistant installation?
Looking online these aren't popular at all, there isn't much documentation or existing HomeAssistant integration. The model name is HTRAM-V1-W.
Using the model name I started looking around and poking to see what I could find, and I stumbled upon this manual
The manual itself contained a QR code which pointed to the android app. That's handy, now my objective is to snoop on the BLE traffic between the android app and one of the devices.
Now of course these were used during COVID, and so there's no support for that app anymore. When I tried to install it on an old android 13 phone, it told me the phone was too recent. So I had to flash the phone to android 12 and cross my fingers that it would work: and it did!
At this point I was finally able to start practising what I had read and learned about BLE reverse engineering 101 (having never done this before). It goes like this:
- Enable Bluetooth HCI snoop logs in the developer settings of your android phone
- Disable then re-enable Bluetooth on your phone
- Start the app, then mess around in the app to try to trigger all the features you're interested in, while meticulously noting what you did in the app.
- Using adb, run
adb bugreportand voilà! you get a zip file that should contain your logs inFS/data/misc/bluetooth/logs
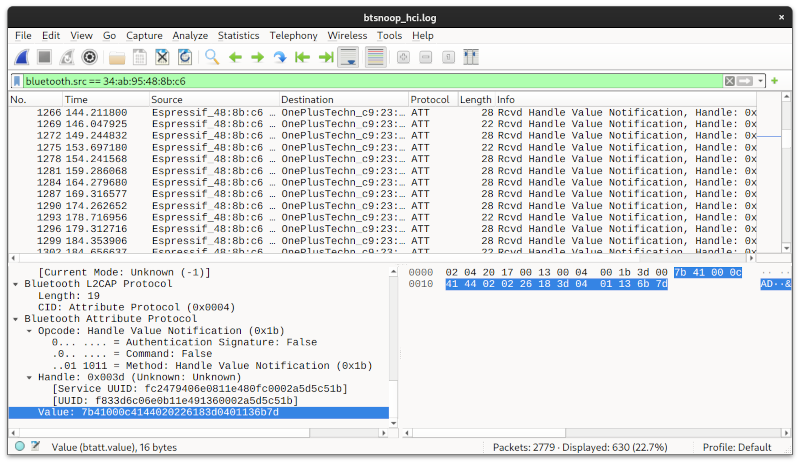
Now what do you do with that file? well apparently you're supposed to load it in wireshark, and guess what network packet correspond to which feature. Here's how it looks like, I find it very intimidating. But at least I've got my log and I should be able to put my thinking hat to figure out the rest another day (or more likely: never)